- At least 59 trusts did not apply critical security patch before cyberattack in May
- More than 80 trusts shut IT systems down to avoid or minimise infection
- Attack resulted in at least 14,778 appointments and 850 operations being cancelled
- Trusts now required to act on critical cybersecurity alerts within 48 hours
More than one in five trusts failed to properly apply security updates that would have protected them against the worst cyberattack in NHS history.
HSJ’s analysis reveals at least 59 trusts did not fully apply Microsoft patches to cover a security vulnerability exploited by the WannaCry ransomware attack on 12 May.
This was despite NHS Digital’s CareCERT team sending an alert to all trusts that said applying the patch, or update, to all supported Windows computers and servers was “critical” in protecting the NHS against a specific cyber threat.
Trusts that reported not applying the security update were disproportionately disrupted in the WannaCry attack.
Our analysis shows the ransomware attack led to the cancellation of at least 14,778 patient appointments and 850 operations across the NHS, as well as numerous tests and scans.
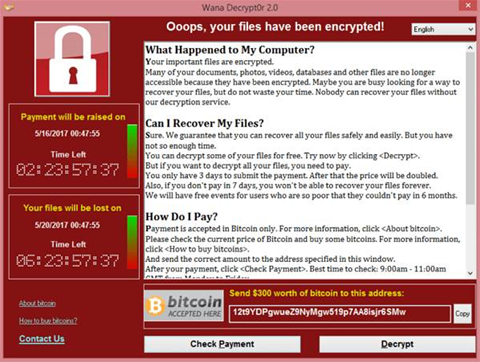
The analysis is based on publicly available trust documents and 163 trusts’ response to HSJ’s request for information. The findings are likely to understate the overall impact of the attack, with several trusts known to be heavily disrupted not responding to HSJ.
The number of trusts that did not apply, or not properly apply, the critical patch is likely to be higher than 59. Overall, 110 trusts did not respond or refused to confirm whether they applied the patch ahead of the attack, with some citing security concerns over revealing the information.
However, HSJ understands our findings are broadly consistent with the picture being reported to national NHS leaders, who are concerned many trusts have not adequately prioritised IT security updates.
Of the 10 trusts most heavily disrupted by the attack (see table below), six confirmed they had not fully rolled out the security update ahead of the attack and declined to comment. Most had started deploying the patch but not finished.
Only one heavily disrupted trust, Barts Health Trust, said it had fully applied the patches. The large London trust blamed its lack of reliance old servers and computers running Windows XP, for which security updates were not available until after the attack.
Other findings include:
- 83 trusts confirmed they shut down their IT systems in response to the WannaCry attack. The majority were not infected and did not report any cancellations of appointments or operations, though many refused to provide figures.
- 38 trusts confirmed there were infected by the WannaCry virus with at least 16,700 computers and servers infected. The government previously said at least 47 acute trusts were infected.
- 34 trusts confirmed cancelling appointments as result of WannaCry with at least 14,778 cancellations across the NHS.
- 17 trusts confirmed cancelling operations with at least 850 cancelled operations.
- The vast majority of reported cancellations occurred at five trusts
Several trusts reported that they had started rolling out the security update ahead of the attack but missed some computers, or delayed applying the update for fear it would making ageing clinical IT systems crash.
To address these concerns, the government made a late addition to its response to Dame Fiona Caldicott’s report on data security, published last week, requiring all trusts to act on CareCERT critical security alerts within 48 hours.
Other measures are focused on making health and social care organisation leaders more accountable for cybersecurity and linking many of these requirements to Care Quality Commission inspections and possible regulatory intervention.
HSJ also understands the Department of Health is considering intervening more forcibly in the purchasing of “core” IT infrastructure, potentially including a new national contract with key suppliers.
The government said it would “work with partners to negotiate a centrally managed agreement with software providers to provide a common core build of an up to date operating system for health and care”. The DH would not reveal further details of this agreement, which is understood to be in the early stages.
Ten trusts most disrupted by the WannaCry cyberattack
| Trust | Number of appointments/operations cancelled | Security update fully applied? |
|---|---|---|
| Northern Lincolnshire and Goole Hospitals FT | 181 | Information not provided |
| Barking, Havering and Redbridge University Hospitals Trust | 295 | No (applied to all applicable PCs, but not servers) |
| London North West Healthcare Trust | 295 | No |
| Chelsea and Westminster Hospital FT | 400 | No (applied to some machines, but not all) |
| Birmingham Community Healthcare Trust | 582 | No (applied to some machines, but not all) |
| East and North Hertfordshire Trust | 922 | Information not provided |
| Derby Teaching Hospitals FT | 1,700 | No (applied to most machines but not all) |
| United Lincolnshire Hospitals Trust | 1,996 | No (applied to most machines but not all) |
| Southport and Ormskirk Hospital Trust | 3,089 | No (applied to all applicable PCs but not servers) |
| Barts Health Trust | 5,125 | Yes |
Note: This includes only trusts that have provided information publicly or to HSJ. HSJ is aware of several trusts that were heavily disrupted by the WannaCry attack that have not disclosed information.
NHS Digital head of security Dan Taylor said HSJ’s analysis highlighted “different levels of preparedness across the system” but should not be treated as a “finger pointing exercise”.
He said: “We recognise that there are many factors that determined how different organisations were affected. We will continue to work with individual organisations across health and care, to help them understand their own unique situation and the steps that they can take to improve their cyber preparedness.”
Mr Taylor said the NHS overall had responded well to the attack, “minimising the effect on patient care”.
However, Saif Abed, founding partner at health IT consultancy AbedGraham, said the data showed even “opportunistic” attacks like WannaCry, which did not specifically target the NHS, could have a serious adverse clinical and financial effects on trusts.
“[These are] costs and losses that can be correlated in the millions before even technical outcomes are factored in,” he said.
Dr Abed said the government response to the Caldicott report was welcome but would require “potent enforcement and incentivisation” to work.
“The government must ensure that standards are unambiguous for NHS organisations to adopt and that inspecting bodies are adequately funded to fulfil their duties,” he added.
Harry Evans, researcher at The King’s Fund, said: “These findings emphasise that cybersecurity is vital to patient safety. The number of operations and appointments that were cancelled as a result of the attack underlines the fact that contingency planning is just as important as cyber-preparedness in protecting patients.”
An NHS England spokesperson said: “Whilst a small proportion of local NHS organisations were affected by the cyber attack, importantly national systems were unaffected and patient data was not compromised.”
Topics
- BARKING, HAVERING AND REDBRIDGE UNIVERSITY HOSPITALS NHS TRUST
- BARTS HEALTH TRUST
- Birmingham Community Healthcare NHS Trust
- CHELSEA AND WESTMINSTER HOSPITAL NHS FOUNDATION TRUST
- EAST AND NORTH HERTFORDSHIRE NHS TRUST
- Finance
- London North West University Healthcare NHS Trust
- NHS Digital (HSCIC)
- NORTHERN LINCOLNSHIRE AND GOOLE NHS FOUNDATION TRUST
- SOUTHPORT AND ORMSKIRK HOSPITAL NHS TRUST
- Sustainability
- Technology and innovation
- UNITED LINCOLNSHIRE HOSPITALS NHS TRUST
- University Hospitals of Derby and Burton NHS Foundation Trust
Exclusive: One in five trusts did not make critical security updates before cyberattack
More than one in five trusts failed to properly apply security updates that would have protected them against the worst cyberattack in NHS history.
 Currently
reading
Currently
reading
Exclusive: One in five trusts did not make critical security updates before cyberattack
- 2
- 3
































2 Readers' comments